Google OIDC Configuration
Pro only
Configuration at Google
-
Open Google Cloud Console
- Make sure to select the correct organization:
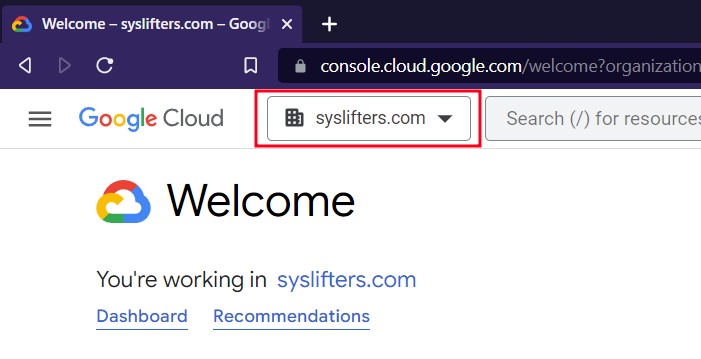
-
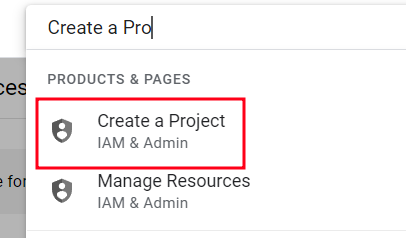
Use search box and click "Create a Project"
-
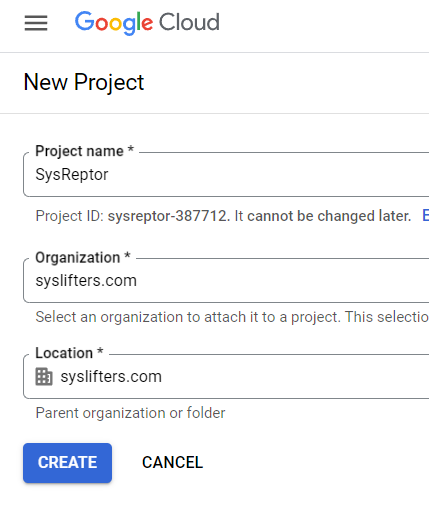
Enter Name, Organization, Location and "Create"
-
Search for and call "OAuth consent screen"
-
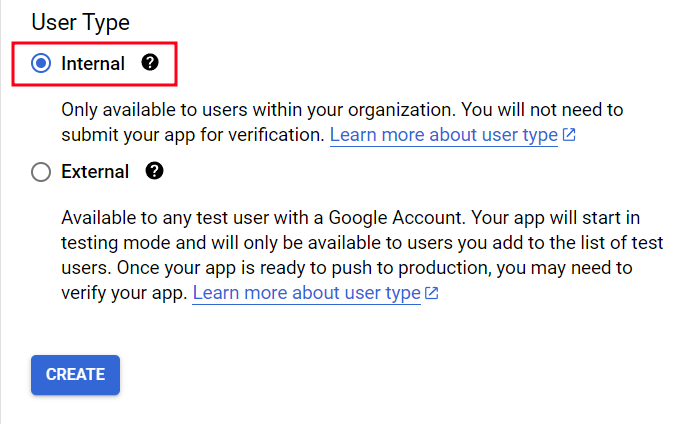
Select "Internal" for "User Type" and "Create"
-
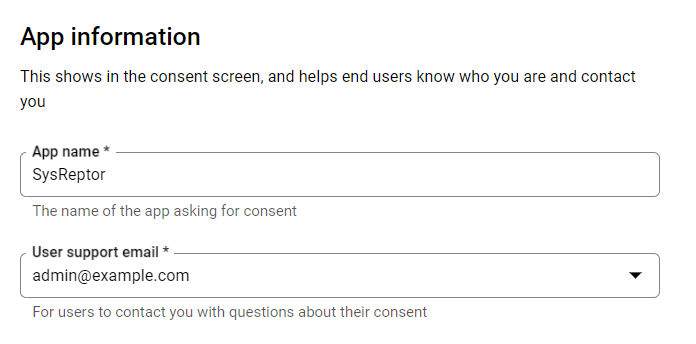
Enter "App information"
-
Optional: Add App logo
- You can use this
-
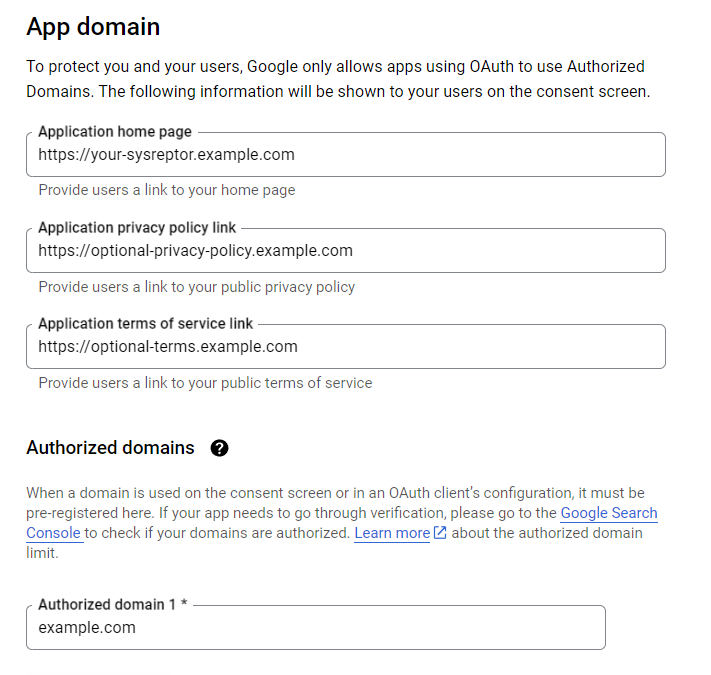
Enter App domain info
-
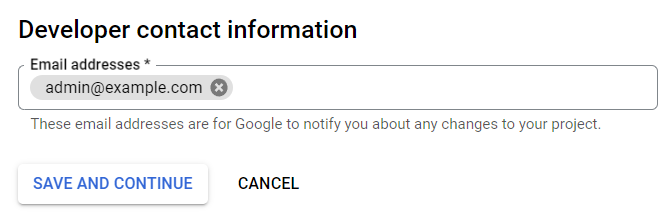
Enter Developer contact information and click "Save and Continue"
-
Add the scopes
email,profile,openid(don't forget to click "Update")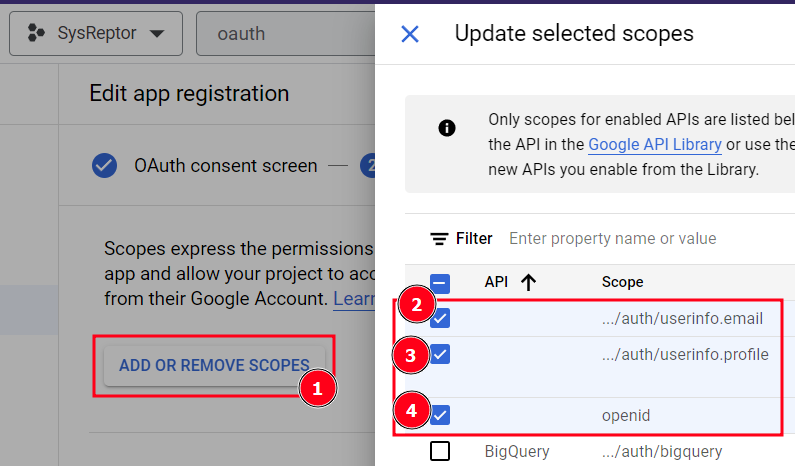
-
Click "Save and Continue" and verify your data
-
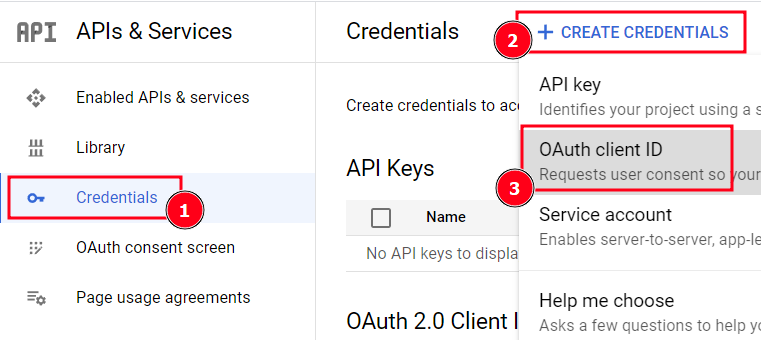
Go to "Credentials", "Create Credentials" and select "OAuth client ID"
-
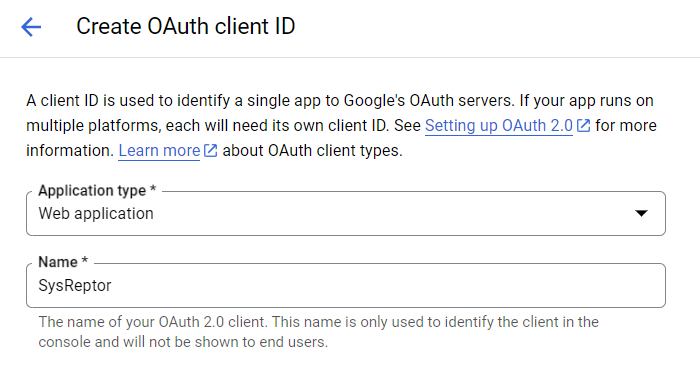
Select "Web Application" at "Application type" and enter a name
-
You don't need any JavaScript origins
-
Enter the URL to your SysReptor installation with the path
/login/oidc/google/callbackas Authorized redirect URI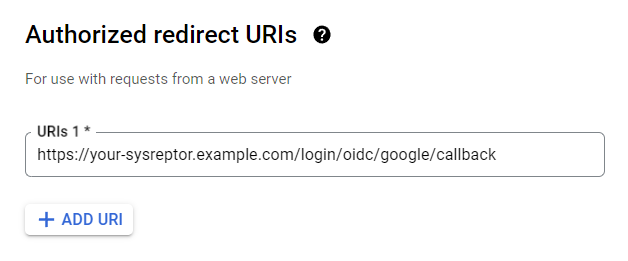
-
Click "Create"
You should now have the following values:
- Client ID
- Client secret
Cloud Setup
Cloud
You are lucky. Just send the values from the previous steps to us and we'll take care
Self-Hosted Setup
Self-Hosted
The values from the previous steps need to be passed as environment variables to the SysReptor docker container.
You can add them to <sysreptor-repository>/deploy/app.env:
1 2 | |
The OIDC client needs to be able to establish a network connection to Google. Make sure to not block outgoing traffic.
Restart the docker container by going to sysreptor/deploy and:
1 | |
Limitations
SysReptor reauthenticates users before critical actions. It therefore requires users to enter their authentication details (e.g. password and second factor, if configured).
Google does not support enforced reauthentication. The reauthentication therefore redirects to Google. If the users are still authenticated at Google, they are redirected back and SysReptor regards the reauthentication as successful.
This is a limitation by Google.
To enforce reauthentication, users can set a password for their local SysReptor user. This will enforce reauthentication with the local user's credentials.